The world today is purely driven by modern technology and gadgets. As much as our life is turning digital, it is exposed to cybercrimes. Cybercrime poses a massive threat to individuals, organizations, and institutions. The Cyber Security tutorial like this throws light on the basics of this threat and how it creates a potential job opportunity for billions.
In a recent development, the U.S. government has warned that cyber-attacks are evolving at a rapid pace. And this is even when the government is spending $19 billion a year. According to the National Institute of Standards and Technology(NIST), the rate at which data is being transferred, it requires real-time monitoring to stay protected against attacks.
The current cybercrimes are being directed by:
1. Single or group attackers that target an organization or individual for ransom or reputation damage
2. Politically driven attacks
3. Attacks that intend to cause fear
Before you venture into Cyber Security by choice, it is important to know the terminology and some basics. That is what this best Cyber Security tutorial for beginners teaches you.
What is Cyber Security & why has it become mainstream?
Cybersecurity is a prevention mechanism against all kinds of cyberattacks. It ensures nobody is exposed to any kind of attack in the online space. This is achieved by building protection systems and protocols for hardware, software, servers, networks, peripheral devices, databases and more.
The IT infrastructure is exposed to risks by both internal and external elements. Some of the important aspects of IT infrastructure have been covered in this Cyber Security tutorials:
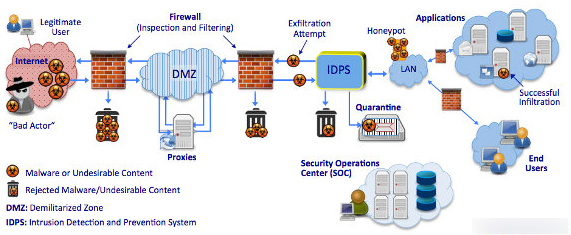
- Network Security
- System Security
- Application Security
- Information Security
- Web Security
- Mobile Security
This is because all of us in one way or another are connected to each other in cyberspace or a network. This offers cybercriminals a honey pot to attack sensitive data pertaining to individuals or organizations.
That is why it has become all the more important to hire experts who can secure systems and networks. This is one of the best Cyber Security tutorials to get the basics right.
It took time, but Cyber Security is now a full-fledged domain that requires programmers, web experts, networks, servers, applications, and cloud experts to ensure complete security.
Here is the video that talks about how to get into Cyber Security as fresher:
What is leading to such a high scale demand of cyber experts?
Cyber-attacks are growing in size and have now turned into global concerns. Organizations are building cyber armies to combat the crimes. And the number of cybersecurity positions across industries have grown by 350% from 2013 to 2021.
According to a report by The New York Times, there will be over 3.5 million unfilled cybersecurity jobs across the globe by 2021.
That is why it is all the more important to understand the basic concepts of cybersecurity with this Cyber Security tutorial for beginners and kick-starting the career in Cyber Security.
Before we learn more about the combat mechanics, it is important to know what kind of attacks are prevalent in the cyberspace.
Best Cyber Security Tutorial to understand Different types of Cyberattacks
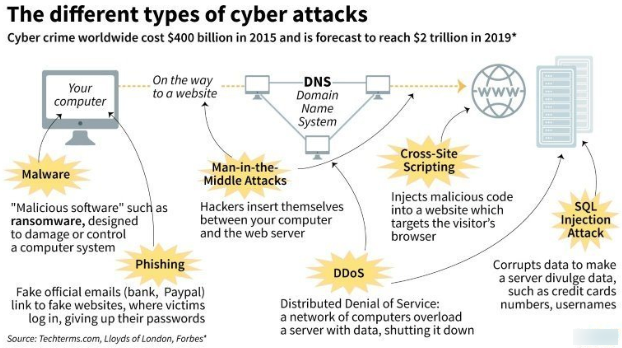
The cyber-attacks or hacks started with attacking a network leading to the performance retardation. But it did not end there. It is not good news but the fact is that cyber-attacks have evolved aggressively and have turned more vast and sophisticated. Some of the very common attacks individuals and organizations have been covered in this Cyber Security tutorials point.
- Phishing
- Malware and Virus-based attacks
- Malvertising
- Man in the Middle
- DoS and DDoS
- Drive-by Download
- Digital Privacy Attacks
What are the different aspects of network & Cyber Security?
Some of the very basics of Cyber Security can be understood only when you understand what security set up includes. Any time a hack is executed, the attacker tries to get hold of the data or information from a system, computer, server, network, server or website.
Special software programs are pushed and executed so that the attacker gains unauthorized access into the system or network. We first need to understand what the different kind of security vulnerabilities and this is the best Cyber Security tutorial for beginners to learn that:
1. Threat
A threat or a cyber threat is the existence of a soft spot in network security. The attacker identifies this spot and tries to enter the system or network through this. Using these points as the gateway, the criminals steal the information or encrypt files to demand a ransom.
2. Vulnerability
The vulnerability can be defined as the weakness in the design of the security system. This might be an error that if identified by the attackers can lead to a security system breach.
3. Zero-Day Attacks
These are very common attacks nowadays. And they have a very high success percentage because these are the vulnerabilities that the system developers are not aware of.
4. Social Engineering
Another very common attack that targets both organizations and individuals. Using this the attacker intends to steal sensitive data of the victim. This data is then manipulated and the victim is attacked via phishing or tailgating.
Cyber Security tutorial for beginners: How to self-train yourself on Cyber Security basics?
The best way to learn Cyber Security is to start from the definitions and understand the basic frequently asked questions. Go through this best Cyber Security tutorial for the most comprehensive read:
1. Trojan
It a complicated threat in today’s time. The financial institutions are generally attacked by Trojan or its sophisticated variants. As these are able to penetrate through antivirus systems without being detected, they pose a serious threat to the financially sensitive information at banks, insurance organizations and the like.
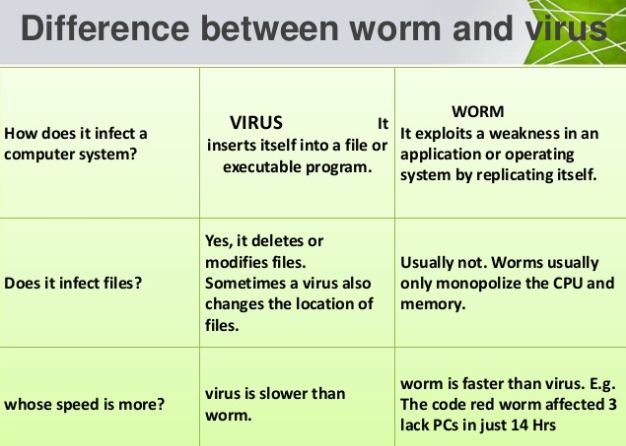
2. Virus
A very old and very common term in Cyber Security. This is a piece of malicious program that tries to damage the files and the system. It is a program that replicates itself and is spread using infected files. But it does require an already infected system. Ransomware is also a kind of virus.
3. Worms
It is a harmless self-replicating program. This is considered to be harmful because it actually keeps on replicating and eats up the hard disk space causing the systems and networks to slow down. These questions are quite basic and might sometimes confuse you. That is why it is very important to go through the Cyber Security tutorials point in detail.
4. Spyware
A kind of Malware that is used by an attacker to spy on a network or a system. Once spyware is injected into the system, the attacker can track each and every activity that is being executed on the system. Based on the information the attacker receives this way, he fabricates an attack that is precisely very identical to the purchases or transactions that you generally do.
5. Scareware
As the name suggests, the program scares the victim and tricks him into purchasing an anti-virus. Once it is installed by the system user, it starts throwing messages on the screen that your system is under attack and throws the victim into a panic. And then it redirects a victim to a bogus website to buy an anti-virus.
6. Keylogger
This program once downloaded logs all the keystrokes of the system. All this data is then sent to the attacking system who then gains the data like user ids, passwords and more.
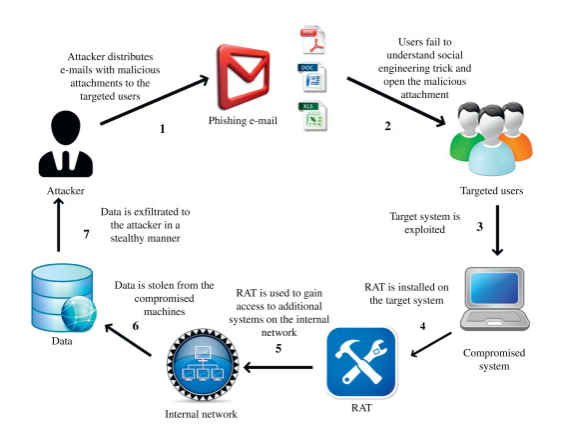
7. Phishing
According to the stats, most of the attacks in cyberspace are directed using phishing attacks. In a phishing attack, the victim is directed to an imposter website that resembles the actual website. It masks a website that actually tries to procure the sensitive login credentials on behalf of the attacker.
There is more about the prevention of phishing attacks in this Cyber Security tutorial. This type of attack is direct on c-level executives to get access to the networks and lead to massive ransomware attacks or data stealing.
8. DDoS
The full form of DDoS is Distributed Denial of Service. In this attack, the hacker sends a multitude of requests to the network, website or server. Once these requests exceed the amount that the entity can handle, the network, server or website collapses and its security is then breached by a simple program.
9. SQL Injection
A malicious program is injected into a server using which the attacker gains access to the database. And once he has a free pass, he can steal/modify any information leading to ransomware attacks. Read the Cyber Security tutorial ahead to learn more about SQL injections.
Difference between Risk, Threat, and Vulnerability?
Threat
Something that can harm a system is known as a threat. A very common example of a threat is a phishing attack.
Vulnerability
It is that weakness of the system that offers threat a gateway to enter and do potential damage. If the system is more vulnerable, the threat has an even bigger impact. Example of system vulnerability is Cross-site scripting and SQL injection.
Risk
It is the amount of damage an organization or individual is exposed to if there are a vulnerability and threat combination.
What is Cross-Site Scripting? How to prevent it?
More commonly known as client-side injection attack. It is a malicious code that executes malicious code on the web browser that is under attack. Here we have covered the prevention also in this Cyber Security tutorial point.
The cross-scripting is prevented by the cyber teams by the following processes:
- Special Character Encoding
- Putting up XSS HTML Filter
- Validation of user inputs
- Using Anti-Cross-Site Scripting tools

What is a Botnet?
A Botnet is a group of devices that are connected over an internet connection. These devices could be servers, PCs or mobile devices. All these are infected by malware that either indent to steal data, lead a DDoS attack or send spam.
What is the CIA?
C: Stands for confidentiality which is a set of rules according to which the access of information is limited across the organization.
I: Stands for integrity which ensures the information across the system is reliable and can be trusted.
A: Stands for availability and ensures reliable data can be accessed only by authorized people.
What is a firewall?
A network or any cyberspace has a lot of traffic (incoming and outgoing data). Thus for the sake of network security, it becomes important to monitor and control this traffic. It is a must to have a question in Cyber Security tutorial for beginners
A firewall is used as a security system. This protects the entry of any kind of malware, viruses or worms and does not allow any kind of unauthorized access into the network.
How is vulnerability assessment different from penetration testing?
While both terms are related to the protection of a network, they both are different from each other. In the process of vulnerability assessment, the system admins define, detect, and prioritize the vulnerabilities.
These are detected across the systems, network or applications. Protocols are created to inform the organization of the way to combat if any attack enters via these vulnerabilities.
On the other hand, penetration testing is also called as ethical hacking. In this, an ethical hacker with authorized access attacks the network and identifies the system vulnerabilities.
How is stored cross-site-scripting different from reflected XSS?
According to industry experts, some of the injected scripts are stored on the victim servers. And these are called stored XSS. They remain undetected and once the victim downloads these scripts, the system is attacked.
In the case of reflected XSS, the attacker has to first send a request. Only then will the script run on the victim’s browser.
What is the need for DNS monitoring?
Using the DNS service, it is ensured that the IP addresses are mapped to a user-friendly domain name. The monitoring of DNS is important to make sure that the traffic is routed properly to the website.
Which is more secure SSL or HTTPS?
SSL (Secure Sockets Layer) is a security protocol. This ensures the communication is secure over two websites and it works over HTTP. The HTTPS (Hypertext Transfer Protocol Secure) inherently combines HTTP and SSL so that the browsing is encrypted. SSL is considered to be more secure than HTTPS. Not every Cyber Security tutorial for beginners answers this question.
What is phishing? How can it be prevented?
In a phishing attack, a fabricated attempted is made by the attacked to derive sensitive information from the victim. This included trying to get usernames and passwords by directing users to a fake website.
Cyber Security experts follow below practices:
- Set up firewalls on the networks and systems
- Updated antivirus protection
- Two-factor authentication
What is SQL injection and how to prevent it?
As a comprehensive Cyber Security tutorial for beginners, we cover SQL injections also. MaliciousSQL statements are used to attack the databases. These SQLs are capable of circumventing security measures thus remain undetected.
Practices to prevent SQL injection attacks:
- Usage of stored Procs(Procedures)
- Validation of user input
- The error message should not show the data
- Keep the system updated
- Credentials must be encrypted and stored in a separate database
Conclusion
We are already witnessing a great boom in the Cyber Security space. And there seems to be no end to it as the attacks are turning more elaborate and sophisticated. The pressing need for more fresher’s and pros to enter the Cyber Security space is growing day by day. On top of it, the existing professionals are required to hone their skills as the field is quite dynamic.
Organizations that are hiring cyber experts prefer freshers with some basic knowledge of the space and the experts who hold credible certifications. The future is bright, the only thing that is required is the skilled workforce.
If you want to build a career in Cybersecurity, enroll yourself in this Cybersecurity Course and become a cybersecurity expert.