Undoubtedly cybersecurity experts have become the most sought after professionals. And the demand is growing exponentially. To build a successful career in cybersecurity you should be aware of ethical hacking interview questions.
According to the Bureau of Labor, the demand for cybersecurity experts is about to witness explosive growth.
The number of jobs is expected to go up by 28% and the salaries offered will break the glass ceiling from 2018-2028.
And to help you penetrate this hype we have the most comprehensive ethical hacking interview questions ready for you.
Over the past two decades, digital footprints have increased exponentially. And there is no looking back. At the current pace, almost 2.5 quintillion bytes of data are generated across the globe every day. All the data is digital with varying levels of sensitivity and privacy.
Thus it becomes mandatory for every organization to protect the data against potential hacks. This is where the role of a cybersecurity analyst crops up. He is the one who ensures the companies digital data that is exchanging hands over the internet stays safe.
Did you know after every 39 seconds there is a hacker attack? To strengthen their security ecosystem against such attacks, organizations appoint ethical hackers to identify the vulnerable security patches.
If you are already a working ethical hacking professional, these ethical hacking interview questions and answers will help you strengthen some basics too.
According to recent data by Indeed.com, a certified ethical hacker can draw an average annual income of $99,000 USD. There is no doubt that the stats sound encouraging. But before one lands up as an ethical hacker professional, he must make sure to chisel his skills.
Moving ahead with the established fact that Ethical hacking has a potential future. Here is the segregated set of question that will help you start from the basics and learn the advanced aspects quickly with this set of ethical hacking interview questions:
Important Ethical Hacking Interview Questions and Answers:
1. What is Hacking?
We are yet to wrap 2019 and Cybercriminals have already earned close to $600 billion. Undoubtedly, hackers are the key players here. The term was coined in 1951 and refers to accessing a system or network without authorized access. The person who conducts the process is called a hacker.
A general modus operandi of a hacker is to steal some personal information of the system or network and demand ransom or use it to steal money.

2. What is Ethical Hacking?
How can hacking be ethical? Well, this term came into play when some hobbyist hackers started helping organizations to identify the network vulnerabilities. And the need is so strong that it has now turned into a full-time role in the security departments. An ethical hacker attacks the network or system with the permission of the network owners. He tries to find the soft spots and then fixes them.
3. Why is the demand for ethical hackers increasing?
According to a study by IBM, the average cost of a data breach has grown up to $3.92 million. Thus more and more ethical hacking professionals are being sought. If you are the one, this Ethical hacking interview questions and answers guide will prove to be a big help
4. Who is a Black Hat Hacker?
Black Hat: This is the category of hackers who makes it to the FBI’s most-wanted list generally. Thus it is clear that they gain un-permission access to the systems and networks with any ill-intent.
5. How is a grey hat hacker different from a black hat hacker?
Grey hat hackers are the ones who penetrate a network or system without the permission of the owner. And once they are into the system, they share the details with the owners. For this either they receive an incentive or do it for the public good.
6. What is a White Hat hacker?
White Hat: Also called the ethical hackers, their aim is to strengthen the security system. While they approach the system or network from a malicious hacker’s perspective, they never intend to do any harm. When you apply for the post of an ethical hacker, most of the ethical hacking interview questions are related to White hat hackers.
7. What is SQL Injection?
Data-driven applications are attacked using SQL statements. These are inserted into an entry field for execution.
8. What is a Brute force attack?
It is a very basic and automated attack to penetrate a website or a network. A hacker tries different usernames and passwords again and again before it enters the system.
9. Is there any other kind of hackers too?
Some of the other hacker terms you might have heard are the Script Kiddie, Hacktivist, Blue hat and red hat hackers. These are hackers who work unethically at a very granular level.
10. What are the different types of hacking?
Before you set out your foot into the ethical hacking territory, you must know what the most common target objects are. And these ethical hacking interview questions and answers will help you get detailed knowledge:
Computer hacking or system hacking was the one where it all evolved. And it continues to happen till today. As we moved a more digital world, hacks like website hacking, network hacking, email hacking, and password hacking started to evolve. The Website hackers try to gain access over the webserver while network hackers try to penetrate the network and grab some sensitive data.
11. What is Cross-site Scripting?
It is a kind of security vulnerability present on the web. This allows attackers to inject client-side script into web pages that are being viewed by other users.
12. What is a Phishing attack?
It is a fraud that is executed using an e-mail. The legitimate-looking email defrauds the readers.
13. What does social engineering mean?
Social engineering is utilizing hacking techniques to acquire sensitive and personal details from a victim.
Email, password and computer hacking is done with an intent to get hold of private data that leads to extortions. As an ethical hacker, one needs to ensure the entire security set-up is immune to these attacks.
Entry-Level Ethical Hacker Job Interview Questions
14. What is the task flow of ethical hacking and why is this the most asked ethical hacking technical interview questions?
Hacking is conducted in 5 primary stages. These stages are:
- Reconnaissance
- Scanning
- Gaining Access
- Maintaining Access
- Clearing Tracks
Every ethical hacker is required to have complete knowledge of all these stages.
15. What does reconnaissance mean in ethical hacking?
This is the phase where all the information is gathered to know the system better. The information varies from determining network range to discover open ports and access points.
16. Are there different types of reconnaissance?
Two types of reconnaissance are active and passive. In active reconnaissance, an ethical hacker is given permission to interact with the system or the network. On the contrary, passive reconnaissance is carried out without any connection to the network.
17. What is defined as Scanning and how is it used in ethical hacking?
Using the data collected in the first stage, a profile of the network to be attacked is created. Three different types of scanning are carried out primarily. These are network scanning, port scanning, and vulnerability scanning.
18. What is Gaining access and how does an ethical hacker do this?
After the reconnaissance and scanning phase, the ethical hacker pins down the tools and techniques to penetrate the system. And this phase is called gaining access, where he is able to gain unauthorized access. As you read ahead you will find many ethical hacking technical interview questions about this stage.
19. How does an ethical hacker maintain access to a network?
A hacker might not be able to get all the information from the network or system at once. He might choose to just stay there and keep extracting data. This is what is achieved during this phase. The malware or Trojan is used to keep the hacker connected and maintain access.
20. What does the clearing of tracks mean and why is it important?
It is important for any hacker not to leave a trail behind. And this is achieved by his includes clearing out the sent emails, server logs, uninstalling apps, deleting folders and any temp files and more.
21. What is a Virus?
It is a malicious program that impacts the performance of the system or corrupts some data. The viruses are spread using an executable file that is shared over email, email attachments or peer-2-peer file sharing. It would require a program to activate it once it enters a system.
22. What is a Worm?
A worm is also a malicious program but it self-replicate and gets into the system over a network or from a file. And it spread rapidly as compared to a virus because it does not require an infected program to propagate it. While preparing the ethical hacking technical interview questions to make sure you know some of the prominent virus and worm attacks.
23. How is a worm different from a virus?
The primary difference between viruses and worms is that the former needs an active host program. That means in order for the virus to do the damage, the system must be already infected and must have an active operating system. On the other hand, worms are stand-alone programs that can cause some type of damage without the help of a host program or human intervention.
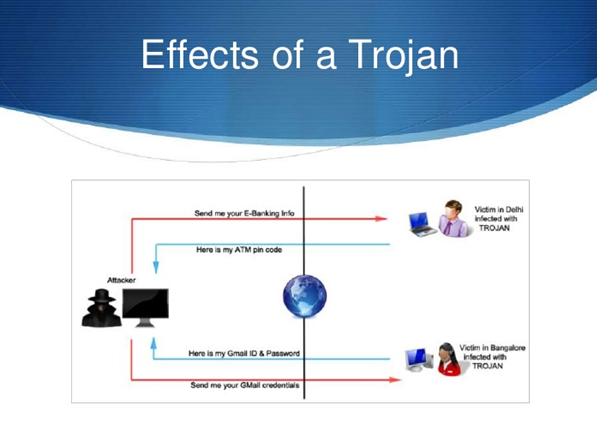
24. What is Trojan?
As discussed earlier, a Trojan malware. This is used at step 3 of the hacking process by hackers to gain access to the network under attack. What might look like legitimate software might be a Trojan! And this is how hackers gain access to systems and networks. The following ethical hacking interview questions and answers will provide you in-depth knowledge. A Trojan might intend to delete/block/modify/copy data or performance disruption of the networks.
25. What is Trojan-Backdoor?
Like every common type of Trojan, it hands over the control of the infected computer to the malicious user. And it is also part of the most common ethical hacker job interview questions. Generally used for criminal purposes, it takes complete control of the system and can send, receive, and delete important files.
26. What does the Trojan-Ransom perform?
It is a type of Trojan program that modifies the sensitive files and encrypts them. And for the decryption or unlocking a ransom is demanded.
27. Why does a hacker require Trojan-Droppers?
It is dangerous and is used by malicious hackers to drop the malware into the system under attack. It requires quite some sophisticated antivirus to detect a dropper.
28. Can Trojan-IM steal private information?
A dedicated program that intends to steal the login credentials of instant messaging apps like Skype and the like.
29. Why can our regular anti-virus not trace the Trojan? What are Rootkits?
It generally accompanies the main malicious program. The task it accomplishes is to hide the tracks and activities of the malware. Thus it supports the malware to operate longer before being detected. In ethical hacking technical interview questions round, you might also be asked about some of the rootkits if you are looking for an advanced role.
30. Can a Trojan be used to conduct DDoS?
Yes, a Trojan- DDoS is the malware that particularly targets the Web-addresses and leads to a Denial of Service from the address.
31. What is hashing?
Using a complex mathematical function a string of text is generated. This text is used to make sure the actual data was not changed.
32. What does encryption mean?
The process of encoding a message so that the person who has the key can only read it.
33. How is hashing different from encryption?
The major difference between the two is that encryption is a two-way process. Once you encrypt some data it is required to decrypt too. An algorithm called the encryption and decryption key is used to secure the piece of data. Get to know more ethical hacking interview questions and answers as you read ahead.
Hashing, on the other hand, is a one-way function. A hash code serves as a check-sum to ensure the data was not corrupted while transmitting.
34. What does the term exploitation mean?
This might be the first of your ethical hacking interview questions list. The hackers need to insert a program into the target network or system to exploit the soft-spots. That said, exploitation is a programmed software or script used by a hacker to take control.
35. How is exploitation executed?
A vulnerability scanner is used to identify the areas that can be exploited and Nexpose, Nessus and OpenVAS are the most commonly used ones.
36. What does enumeration mean?
The process of getting access to information like user names or network is known as enumeration. The hacker needs to establish an active connection with the system to get the maximum possible information. As a part of Scanning, it is used to get important information to exploit a system.
37. What kind of information is collected during enumeration?
Generally, the important information collected during this phase is:
- User and group names
- Network Resource and shares
- Machine names
- Applications
- SNMP details
- DNS details
Advanced Level Ethical Hacking Interview Questions
38. What does defacement mean?
A very common attack on webpages and that is why it is present in our ethical hacking interview questions and answers list. It uses SQL injection attacks. If the input fields are not initialized, the hacker can use SQL strings to create a query.
39. What happens when defacement is executed?
Once the query is executed, the website may reflect defaced data thus impacting the visual appearance of the website. It is generally conducted by hacktivist groups.
40. What is footprinting?
The process by which an attacker gains maximum possible information about the target system. This helps primarily to make the attack successful. During this phase, a hacker gets to know the security posture, identify the attack area and vulnerabilities and draw a network map.
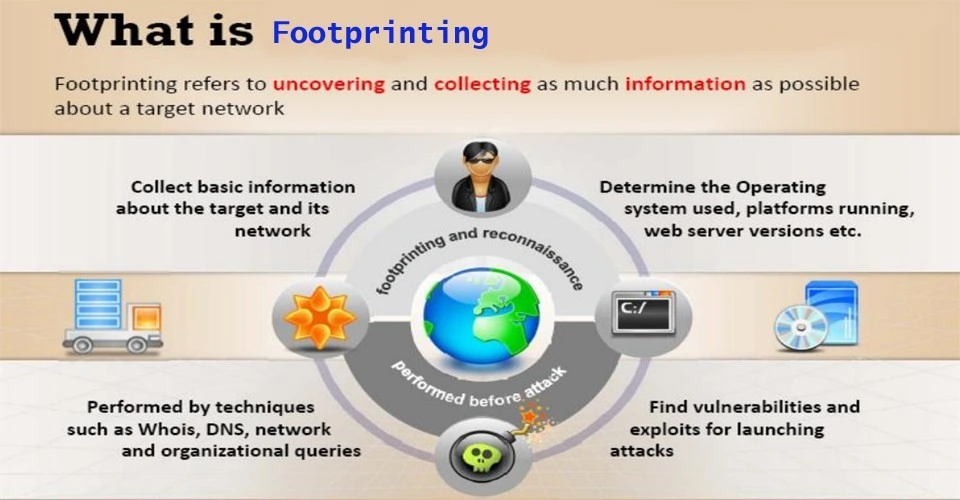
41. What information is collected while footprinting?
The kind of information that is generally collected is IP address, VPN, URL, email id, password and server configurations.
42. What are the different types of footprinting?
Active and Passive footprinting are two types of footprinting used to collect the data. Both differ in the way they connect to the system under attack.
43. What do you mean by fingerprinting?
Before the attacker drops a malware or malicious program, he needs to identify the kind of operating system that needs to be penetrated.
44. What are the different elements that need to be looked upon while fingerprinting?
An ethical hacker uses the fingerprinting technique by looking for four important elements.
- TTL
- Window Size
- DF
- TOS
45. What is active fingerprinting?
To conduct active fingerprinting, specially crafted packets are sent to the target machine. The response and data gathered are then used to identify the OS. The NAMP tool is used to conduct active fingerprinting.
46. What is passive fingerprinting?
Passive fingerprinting: From a remote system, packets of sniffer traces are sent to the system under attack. After analyzing these sniffer traces, the OS is identified.
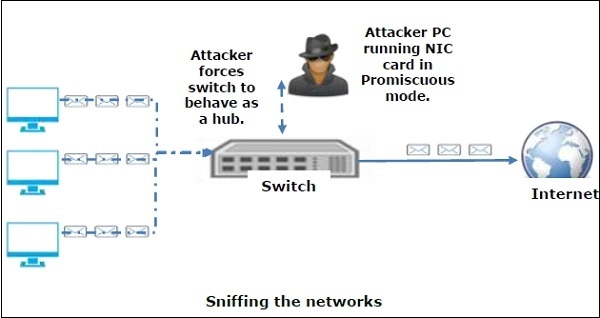
47. What is sniffing in ethical hacking?
A very common technique of monitory the information passing through a network. The hackers use this technique to capture data and extract sensitive information from the same.
48. What does active sniffing mean?
Using this technique the hackers can lock, monitor and edit the traffic or data.
49. What does passive sniffing mean?
This technique allows the attackers to lock the information. And this is information is then made available to a network segment where it can be exploited.
50. What are some common sniffing tools?
Some of the very common sniffing tools are Tcpdump, Wireshark, Fiddler, EtherApe, Packet Capture, NetworkMiner and more.
51. What are the popular tools used for ethical hacking?
Every ethical hacker or his organization has a set of choicest tools to conduct the process. Some of the most popular ones are:
- Metasploit
- Nmap
- Wireshark
- SQLMap
- IronWASP
- Nikto
Conclusion
It is always a MUST to prepare well before your interviews. If you have any certification in ethical hacking that is definitely a big plus for you.
Placing these highlights of your career in the right place is very important. But to sail through any kind of interview test, you must prepare yourself well. I hope this list of interview questions from experts helps you grab that lifetime opportunity.
If you are an aspiring ethical hacker, grab the opportunity to start your career in Ethical Hacking. Enroll in our Cyber Security Course and kickstart your career as an Ethical Hacker.








